It can be extremely challenging for security teams to detect and respond to CEO fraud. As traditional security gateways and perimeter defenses are often ineffective against this vector, security teams rely upon employees to spot CEO fraud-related emails. In this post, we explore how the Tines Security Orchestration Automation and Response (SOAR) platform can be used in conjunction with out-of-the-box features provided by GSuite and Microsoft Exchange to amplify CEO Fraud detection and response.
What is CEO Fraud?
In a typical CEO fraud attack, a malicious actor will impersonate your organization’s CEO or another senior executive. They will send an email to a member of your staff and attempt to convince them to wire funds, or, as in a recent wave of attacks, send gift voucher codes.
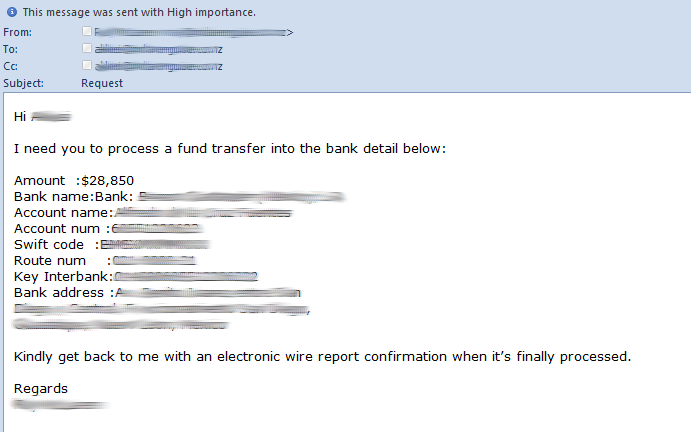
CEO Fraud Sample Email
CEO Fraud Email from SpiderLabs
To make their attacks more convincing, malicious actors research their targets up-front. Using LinkedIn, Twitter, Facebook, etc., the fraudsters glean information like email addresses, roles, and locations. If the cybercriminals are looking for money, they may target staff in the accounts payable department. If they are looking for tax information, they may target human resources.
Why is CEO Fraud difficult to detect/prevent?
Unlike standard phishing, CEO fraud emails are unlikely to contain malicious links or attachments. As such, they will likely pass through traditional email gateways. Additionally, email validation systems such as DMARC may not prevent the delivery of CEO fraud emails either as attackers may not spoof your company’s domain directly; sending the malicious email from your-c0mpany.com (with a zero) rather than your-company.com.
As the CEO fraud email will likely originate from outside your organization, displaying a warning to the recipient indicating the message is from an external source may be helpful. However, if the target receives many external emails, it’s likely they will habituate or “tune out” security warnings like the below.
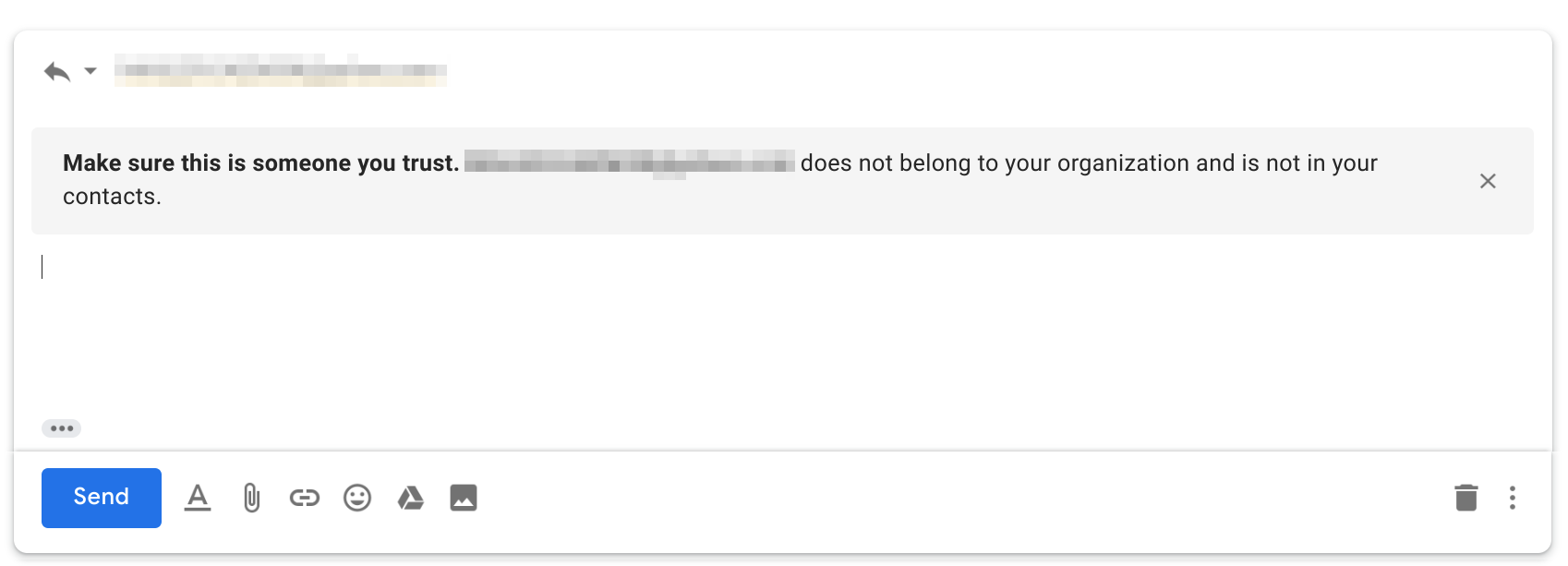
Replying to external sender example
Using Tines to automate response to CEO fraud
Using G Suite content compliance or Exchange Transport rules we can create a list of keywords and/or regular expressions that are common in external CEO fraud emails. A list of useful keywords is available in this Git repo, however, the most important ones are your CEO and senior executives’ names. If an email originates from outside your organization and claims to be from your CEO or a senior exec, forward a copy to your monitoring inbox.
Use a Tines IMAP Action to read emails flagged as CEO Fraud
The Tines IMAP Action will emit events when it detects new emails in a specified inbox.
When an emitted event is related to a potential CEO Fraud email. The IMAP Action will emit flagged emails in events similar to that shown below. Here we can see the fraudster is using a Gmail account to impersonate our CEO, Kate Jones.
Automating victim reach out
When an event is emitted, we can use a simple Email Action to contact the targeted employee and warn them that they may be in correspondence with a fraudster. We could also send the employee an instant message. Let’s use Slack to demonstrate how this could work.
The following HTTP Request Action will find an employee’s Slack profile from their email address:
When the above Action runs, the emitted event will contain an “id” field which we’ll use to contact the target via DM.
Next, we’ll use another HTTP Request Action to contact the user on Slack. Our Slack message will warn them that they received a suspicious email. We’ll also include a Prompt widget so that they can let us know whether the email was expected. The options block for this HTTP Request Action is shown below.
Now, when one of our users receives a potential CEO fraud email, seconds later, they will receive a Slack message similar to the following:
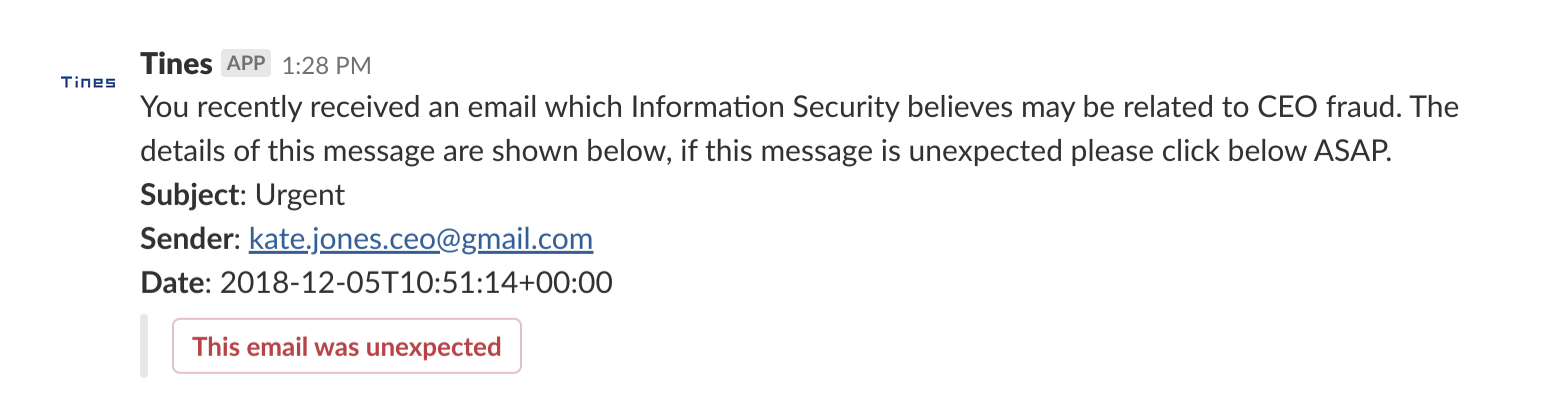
Slack CEO Fraud notification via Tines
When the “This email was unexpected” button is clicked by the user, Tines emits a corresponding event. The automation Story can then continue in any number of ways, for example:
Create an incident ticket in InfoSec’s case management system.
Page the InfoSec on-call responder if out of hours.
Blacklist the malicious sender.
Share the email address as an IOC with peers.
Conclusion
For Information Security teams, detecting and responding to CEO fraud can be challenging. However, by leveraging Tines and tools you already have at your disposal, i.e.: G Suite content compliance and Exchange transport rules, we can quickly flag and automate security response to suspicious emails.
As always, with the Tines Advanced Security Automation Platform, it’s easy to adjust automation stories as our processes adapt and our capabilities mature. For example:
Before contacting the user, check if the sender has been seen in our environment in the last 30 days.
Add additional response options in the Slack message for “This email is legitimate” and “I’ve already replied to this email”.
If a user interacts with a CEO fraud email, send them security awareness content.
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*