This is the first blog in a series looking at how companies are consuming and sharing threat intelligence using Security Orchestration and Automation platforms like Tines.com.
In this blog we discuss the process of sharing individual indicators of compromise (IOCs) using tines.io. With Tines it’s easy to share IOCs to common Threat Intelligence platforms like AlienVault, Trustar, Facebook Threat Exchange and PassiveTotal as well as automating sharing IOCs on Pastebin and submitting content to VirusTotal, urlscan.io and Phishtank.
Most information security teams have dozens of security tools, and with dozens of threat intelligence platforms available [0] it’s hard to know which one suits your company best. Unfortunately it’s not always clear which Threat Intelligence tools integrate with other tools in your security stack. Furthermore, it’s important to know which tools your peers and partners are using to share relevant threat intelligence for you can consume. Consequently, the best advice centers around using platforms which are used by your peers. Hence, platforms which have a Rest API for easy sharing, classification and integrations usually have the most use and highest quality indicators. It’s also important to investigate threat intelligence platforms which can link with your SIEM, Endpoint Tools, Firewalls etc. These links can help your security teams detect and block malicious attacks.
Features of Good Threat Intel Platforms
In order for any platform to be successful security teams and analysts must be comfortable using them frequently to keep indicators up to date. Likewise, they require participation and active sharing of threat intelligence by other security teams, either publicly by security vendors or altruistic companies, or privately by ISACs or industry groups, when they come across it.
One of the advantages of the tines.com security automation platform is we don’t rely on any pre-built integrations. Consequently, consuming and sharing to a new threat intelligence source or feed is as simple as signing up for an account, creating an API key, or sending an email. Therefore there’s no need to wait for your SOAR vendor to build an integration or to build one yourself.
This blog discusses how you can use tines.com to automate the sharing of malicious IOCs of your own to multiple threat intelligence platforms.
How to Share Indicators in Tines
Tines provides pre-built stories for security teams to help them automate threat intelligence sharing. In contrast to one-off scripts, using Tines can automate the sharing of indicators with not one but dozens of Threat Intelligence platforms at the same time. We can also easily add other platforms without the need for additional coding or development. The below Story shows just how easy it is to share Threat Intelligence Automatically to a handful of different threat intelligence sources:
AlienVault
Trustar
Phishtank
URLScan.io
VirusTotal
Pastebin
Facebook Threat Exchange
RiskIQ PassiveTotal
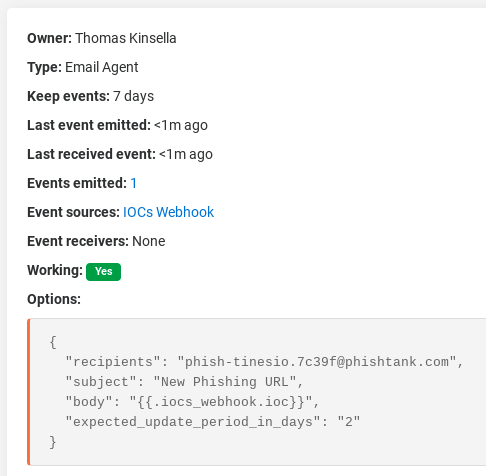
In the example below we have created a Story “Share Indicators of Compromise” and an Action called “IOCs Webhook”. To start this Story we’re sending the webhook an event with a malicious URL, along with an indicator type, indicator group, name and a tag. To read more about how to create a Story in Tines click here. In addition, you can download the Story below and upload it to your own community edition tenant.
You can generate data in your own webhook via a form or using a simple curl command.
Subsequently, your webhook will receive the below event:
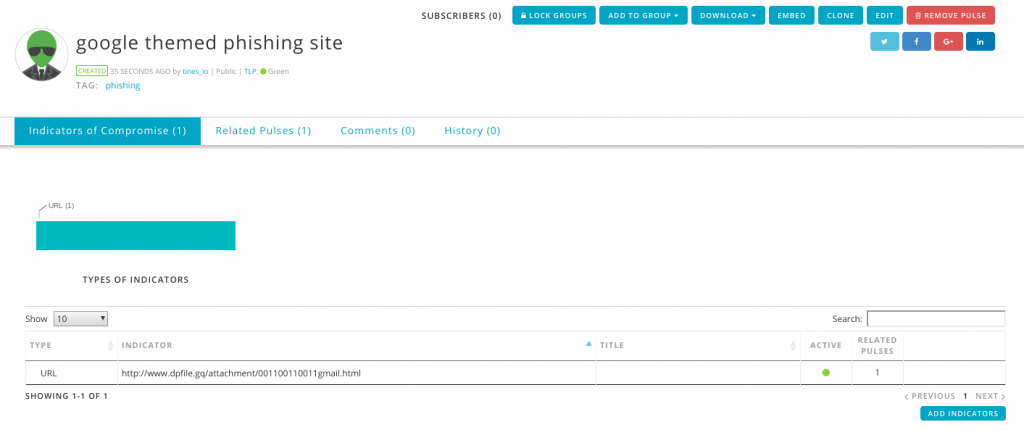
AlienVault is one of the largest online threat intelligence platforms with over 65,000 participants who contribute more than 14 million threat indicators daily. Data in Alienvault is shared through “Pulses”. Pulses provide a summary of the threat and group related indicators of compromise (IOC) together. You can create a pulse in AlienVault with a simple curl request.
Similarly, to create a pulse using Tines with the data sent to the webhook, you can create a HTTP Request "Post" Action. When we add the webhook as an “Event Source” this Action receives the event emitted by the webhook Action, and can read the event’s parameters and be referenced using the json path of those parameters. For example, adding {{.iocs_webhook.ioc}} to the HTTP Request "Post" Action will send through the URL in the image above in the “name” parameter of the payload. Similarly, {{.iocs_webhook.ioc_type}} will pass through the type above, “url” as the indicator type to AlienVault. This Action then sends the relevant information to AlienVault:This simple request automatically creates a Pulse in AlienVault OTX. This pulse is public and contains all the information we originally sent to the webhook above:AlienVault OTX – Creating Pulses. A pulse created using tines.com here. Trustar is another threat intelligence platform popular among “Information Sharing and Analysis Centers” (ISACs) like IT-ISAC or H-ISAC (Health-ISAC). They provide closed-source feeds from entities like Abuse.ch, DHS CISCP, US-Cert, Malware Traffic Analysis and others that can be integrated into your SIEM, Splunk, Endpoint tools etc. Once you have a bearer token, you share data with Trustar using curl: You can augment the above query to send pulses with hundreds of IOCs or update a pulse with more information using a “Patch” command.To submit to IT ISAC you need an Enclave ID to which you have “Full Access” and then include that in your request. You’ll also need to login or create an OAuth2.0 App to get a Bearer token which is included in your request, as below. Trustar – Sharing IOCs to an EnclaveFor a full list of ways to submit data to AlienVault OTX you can read their full documentation.
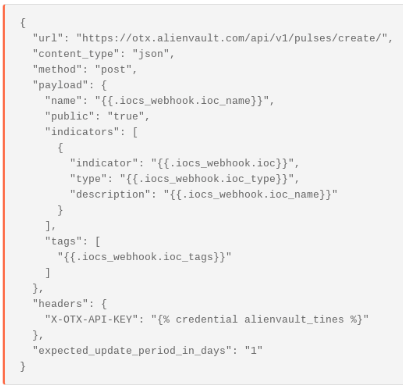
This simple request automatically creates a Pulse in AlienVault OTX. This pulse is public and contains all the information we originally sent to the webhook above:
You can augment the above query to send pulses with hundreds of IOCs or update a pulse with more information using a “Patch” command.
For a full list of ways to submit data to AlienVault OTX you can read their full documentation here.
Trustar – Sharing IOCs to an Enclave
Trustar is another threat intelligence platform popular among “Information Sharing and Analysis Centers” (ISACs) like IT-ISAC or H-ISAC (Health-ISAC). They provide closed-source feeds from entities like Abuse.ch, DHS CISCP, US-Cert, Malware Traffic Analysis and others that can be integrated into your SIEM, Splunk, Endpoint tools etc.
To submit to IT ISAC you need an Enclave ID to which you have “Full Access” and then include that in your request. You’ll also need to login or create an OAuth2.0 App to get a Bearer token which is included in your request, as below.
Once you have a bearer token, you share data with Trustar using curl:
curl -k -H "Content-Type: application/json" -X POST -d '{"enclaveIds":["c04caa4e-4d1b-47fc-b9e2-c9ce11396b44"],"content":[{"value":"55.66.77.88","sightings":32,"source":"internal","notes":"internal IP","tags":[{"name":"indicator-tag-1","enclaveId":"c04caa4e-4d1b-47fc-b9e2-c9ce11396b44"},{"name":"indicator-tag-2","enclaveId":"c04caa4e-4d1b-47fc-b9e2-c9ce11396b44"}]}],"tags":[{"name":"api-tag","enclaveId":"c04caa4e-4d1b-47fc-b9e2-c9ce11396b44"}]}' -H "Authorization: Bearer {access_token}" https://api.trustar.co/api/1.3/indicatorsIn Tines, a HTTP Request Action is used to make a "Post" request to the Trustar API. Similar to the AlienVault Action we are sending Trustar data that was sent to the webhook above:

When Tines runs this Action, the relevant indicator is shared to Trustar. Because we chose an ISAC enclaveID, this indicator has been shared with our partners in the relevant ISAC. We could also share the indicator in our own private enclave.
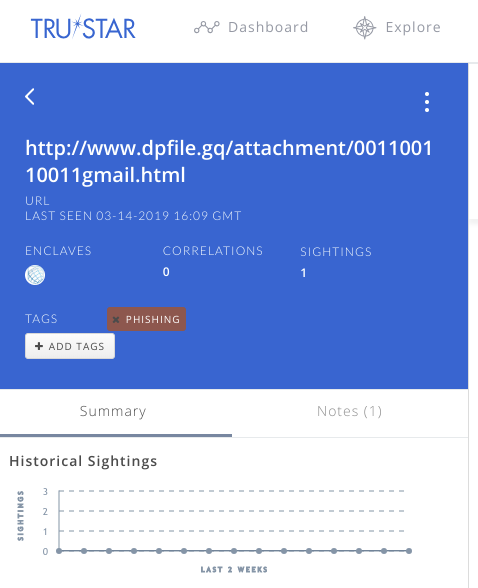
You can also update indicators, delete indicators, share contextual information and more using the Trustar API in Tines. For a full list of ways to submit data to Trustar you can read their full documentation here.
Phishtank – Submitting Phish
Phishtank is a large, collaborative, public repository of online phishing websites managed by OpenDNS.
In contrast to AlienVault and Trustar, Phishtank to not have an API for submitting malicious URLs. They do, however, provide a mechanism submit URLs via email directly. When you create a Phistank account you receive a private submission email address:
An indicator shared in a Trustar Enclave
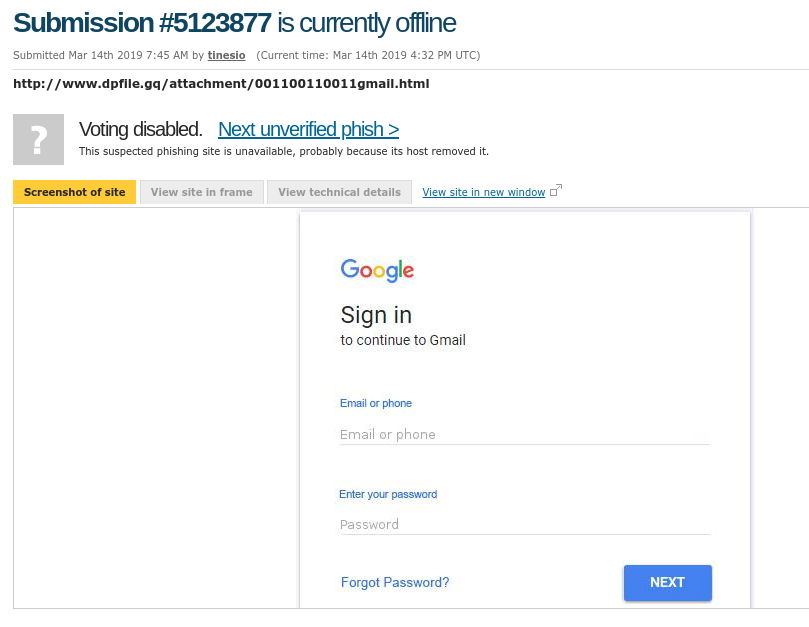
In Tines, we can create an email Action to submit the malicious URL as part of the email body: The configuration for an Email Action to submit data to phishtank. Using Curl you can submit a URL for public sharing and analysis using the below command: To read more about reporting Phish to Phishtank click Urlscan – Sharing URLs. Phishtank is smart enough to extract URL, scan it, and allow community voting on whether or not it is malicious: Urlscan.io is a free online service which scans and analyse websites. Due to its widespread use and quality of the data it is becoming one of the most popular threat intelligence platforms. Urlscan has an easy to use Rest API, and submitting URLs for scanning is straight forward. To get started you need to sign up for a free account and request an API Key.
To read more about reporting Phish to Phishtank click here.
Urlscan – Sharing URLs
Urlscan.io is a free online service which scans and analyse websites. Due to its widespread use and quality of the data it is becoming one of the most popular threat intelligence platforms. Urlscan has an easy to use Rest API, and submitting URLs for scanning is straight forward. To get started you need to sign up for a free account and request an API Key here.
Using Curl you can submit a URL for public sharing and analysis using the below command:
curl -X POST "https://urlscan.io/api/v1/scan/" -H "Content-Type: application/json" -H "API-Key:$apikey" -d "{"url":"$http://badsite.com", "public":"on"}"Similarly, the sample Action configuration for submitting to urlscan.io is straight forward:
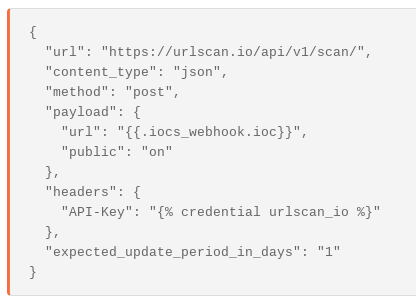
This will publicly submit the URL we sent to the webhook to urlscan.io:
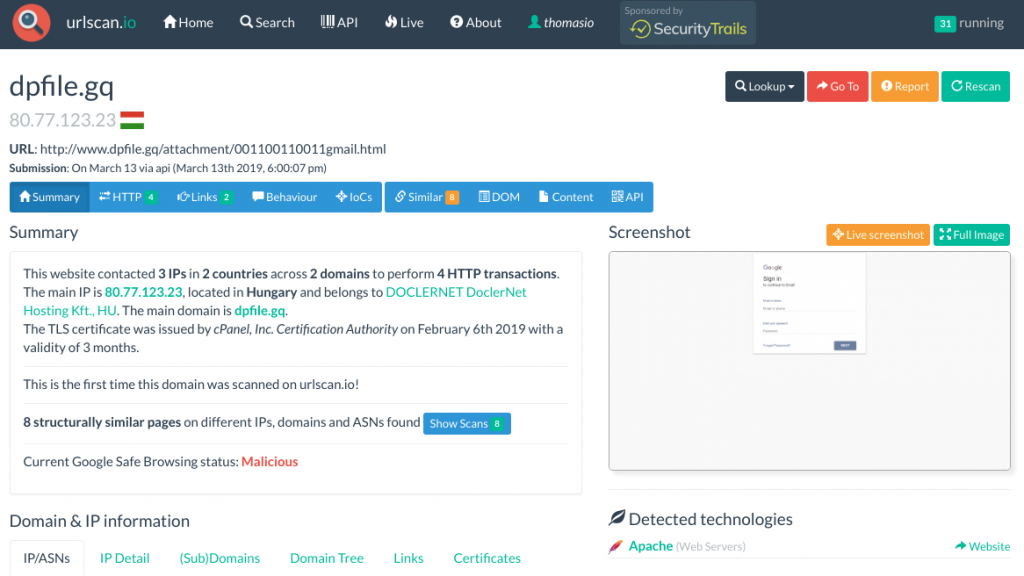
For a full list of urlscan.io API commands and documentation click here.
VirusTotal – Sharing IOCs
Similar to Urlscan.io, VirusTotal is another one of the most popular threat intelligence platforms for sharing intelligence publicly. All urls submitted publicly are shared and analyzed by up to 60 different anti-virus engines. They are given an aggregate score based on the number who detect the URL as malicious.
Through Tines it’s simple to integrate with the VirusTotal API as outlined previously here. To submit a URL to VirusTotal using curl you can use the below command:
curl --request GET --url 'https://www.virustotal.com/vtapi/v2/url/report?apikey=<apikey>&resource=<resource>'We can use a HTTP Request Action to submit a "Get" request with the URL in the same way:
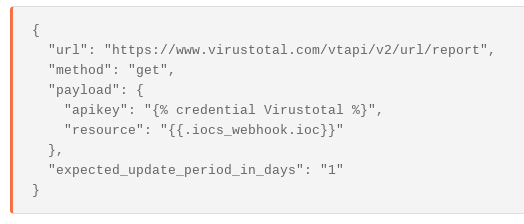
Submitting to VirusTotal allows over 60 different anti-virus companies to scan the page.
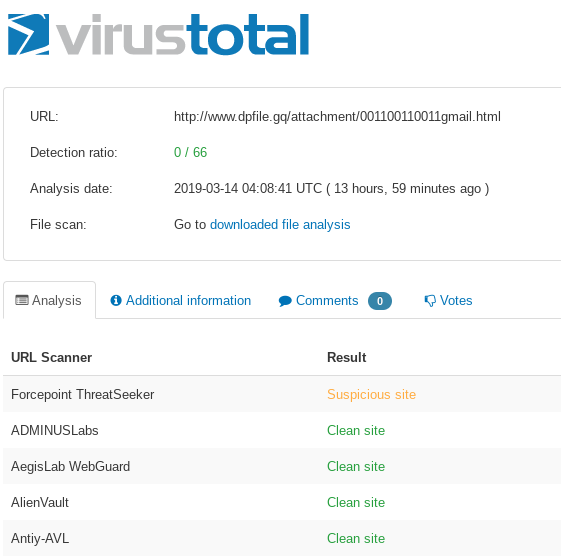
To read more about the VirusTotal API click here.
Pastebin – Creating Pastes
For large scale malware and phishing campaigns, several threat intelligence and malware researchers share indicators on the Pastebin platform. For instance, researchers frequently share indicators from Hancitor, Trickbot, Emotet, Ursnif and others campaigns for security teams to analyze and track.
Automating the sharing of indicators to Pastebin is free and easy. Once you sign up for pastebin account you should generate a “userkey”. You can do this with your username, password and API Developer Key which is available in the API Documentation. Pastebin have created an easy form to generate the userkey here.

After generating the userkey, you can create a paste using curl.
Similarly, using the API Developer Key and Userkey, you can create a HTTP Request Action to create a Paste on Pastebin using Tines:
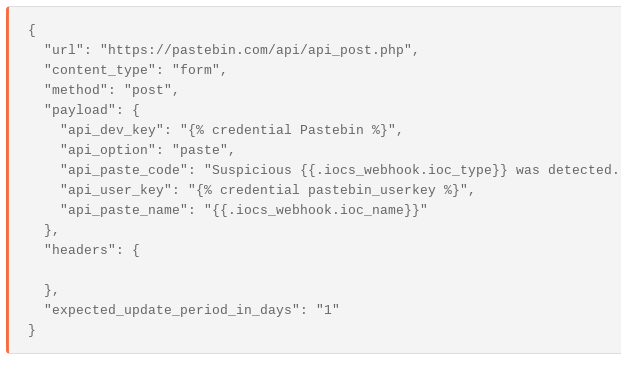
This will result in a public paste with the Indicator and some context:
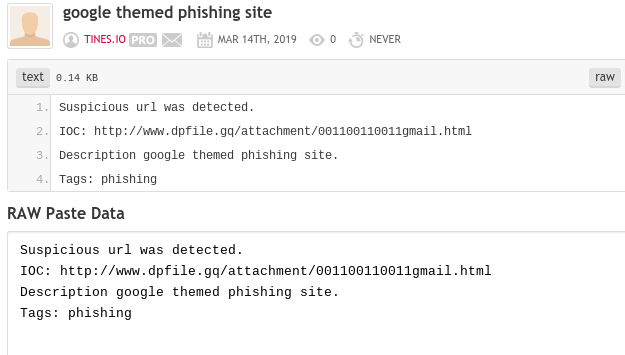
You can read more about the Pastebin API here.
Facebook Threat Exchange – Creating Indicators
Facebook Threat Exchange is a private threat intelligence api for security professionals to share threat intelligence more easily, learn from each other’s discoveries, and make their own systems safer. It is built on Facebook Graph, and has over 800 members who share and submit indicators publicly and privately.
Unsurprisingly, submitting indicators to threat exchange is easy using the Facebook Graph API:
curl --request POST --url 'https://graph.facebook.com/threat_indicators?access_token={{AppID}}|{{AccessToken}}' --form indicator=evil-domain.biz --form type=DOMAIN --form threat_type=MALICIOUS_DOMAIN --form status=MALICIOUS --form 'description=This is a malicious domain.'Likewise, to share indicators in Facebook Threat Exchange through Tines we can create a HTTP Request Action with the below configuration:

This will then submit the content publicly to Facebook Threat Exchange:
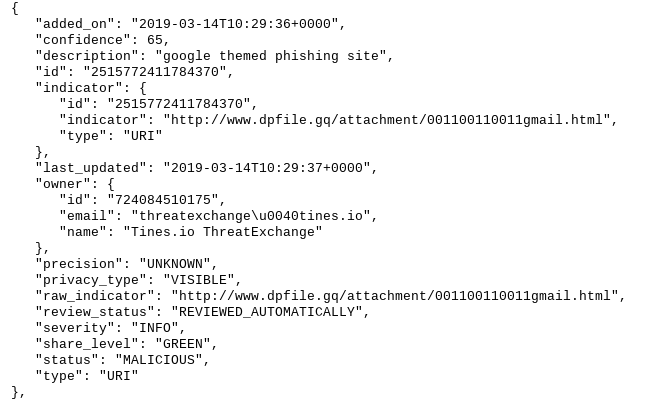
With Facebook Threat Exchange it’s also possible to submit privately, or submit to specific industry sharing groups you’ve created. Furthermore, if you make a mistake you can easily update the indicator and mark it as non-malicious.
For a full list of ways to interact with Facebook Threat Exchange you can read their documentation here.
RiskIQ PassiveTotal – Creating Artifacts
RiskIQ PassiveTotal is another popular threat intelligence platform which has integrations with Splunk, QRadar, McAfee SIEM, Check Point Firewalls and dozens of other security tools. By sharing with RiskIQ you can often integrate directly into your own tools, in addition to helping the RiskIQ security community.
Before submitting any data to RiskIQ you have to create a Project, however this can be done using the UI, or using the API. An Action to create a public project using the RiskIQ API is included in the downloadable Story. Once you have created a project you can easily add IOCs to that project using the curl command below.
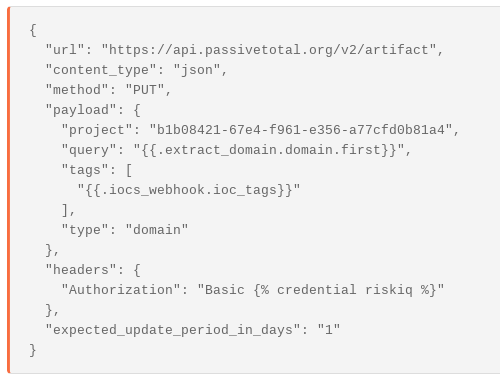
$ curl -u $USERNAME:$KEY 'https://api.passivetotal.org/v2/artifact' -X PUT -H "Content-Type: application/json" --data '{"project": "f083816f-9769-16cb-4660-4b389dc3ae67", "query": "example.org"}'In Tines, we can create a HTTP Request Action to do the same thing, however as PassiveTotal relies on domain intelligence rather than URL intelligence we first use a Tines Event Transformation Action to extract the associated domain. This Action configuration is also included in the downloadable Story. Once the domain has been extracted it’s easy to share the URL in PassiveTotal using a HTTP Request Action:
This will create an IOC in the associated RiskIQ Project.
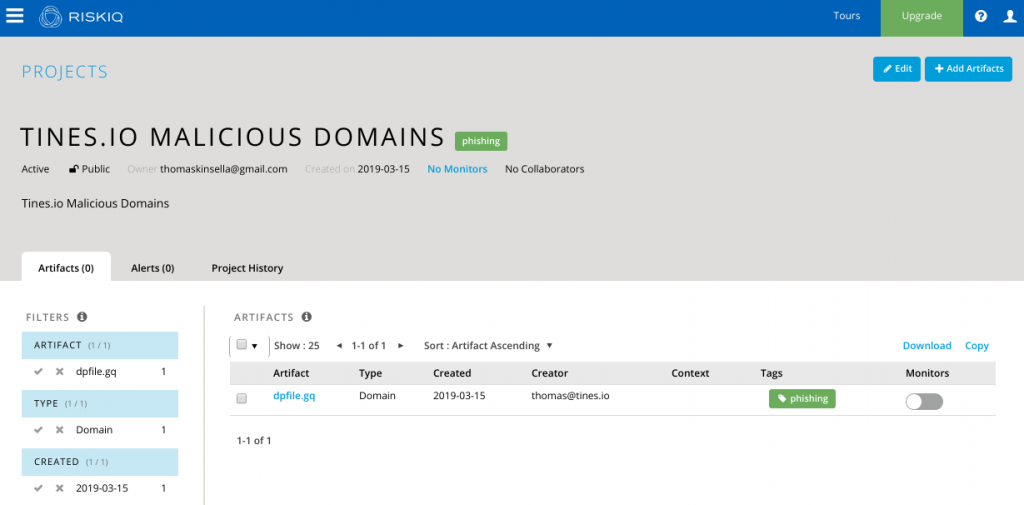
You can read more about the PassiveTotal API here.
Conclusion
Using Tines it’s easy to automate the sharing of indicators to dozens of threat intelligence platforms in addition to the above eight. To download this Story for your own Tines tenant to see how easy it is for yourself, please click here. The completed Story looks like this:

Sources:
[0] Cyberscape Threat Landscape https://momentumcyber.com/docs/CYBERscape.pdf
*Please note we recently updated our terminology. Our "agents" are now known as "Actions," but some visuals might not reflect this.*