Performing malware analysis on suspicious files is a bread-and-butter activity of any security operations or incident response team. Whether submitted to an abuse inbox, caught by an email gateway, detected by anti-virus, or found during a breach investigation, the malware analysis process is time-consuming, repetitive, and manual – which is why many teams are examining malware analysis automation.
There are dozens of approaches to analyzing potentially malicious files and binaries, including static and dynamic analysis. For now, at least, nothing will perform better than a sophisticated malware reverse engineer interacting with and analyzing a file manually in a secure environment. However, relying on some form of automation is necessary until humans can work at the scale and speed of malware analysis engines.
One of the most popular methods of Malware Analysis Automation to determine the maliciousness of suspicious files is using public and private sandboxes. Popular sandboxes include Any.Run, Hybrid Analysis, Joe Sandbox, Valkyrie Sandbox, Cuckoo Sandbox. In this blog we examine some private and public sandboxes that analyze suspicious files. We’ll also learn how the results of the analysis can help proactively protect our environments.
Firstly, a word of caution, at Tines, we don’t want you to think that you can completely automate the process of securing your environment by analyzing suspicious files. There are dangers and pitfalls to completely automating the analysis of malware. Modern malware often requires multiple applications to be running on a box for the malware to be triggered. Other malware can detect that it’s running in a sandbox. Furthermore, in many cases, different contamination levels will require different triggers. Automated sandboxes struggle to accurately simulate the activities of a real, infected end-user. However, several sandboxes like app.any.run allow interactive analysis with malware and may help in this regard.
When should I automate the analysis of malware?
Using a Sandbox is the right approach for frequent, repetitive malware analysis tasks. A good example of a process like this is analyzing files that AV software detects as suspicious. Attachments that users submit to an abuse mailbox are another source of files that frequently require non-sophisticated malware analysis.
There are several free, public sandboxes available online, however, if you suspect that a suspicious file may be targeted at your organization directly, you should consider using a private sandbox. This will help prevent a targeted attacker from knowing you have detected their activity.
You can set up a free private sandbox like Cuckoo Sandbox, or you can make a private submission to sandboxes like app.any.run, hybrid analysis or other commercial sandboxes like the Crowdstrike Falcon or Palo Alto Wildfire.
How can I upload files programmatically?
Uploading files to app.any.run, cuckoo, or hybrid analysis from Tines is simple once the file's contents are in Tines. Tines can read the contents of email attachments or, in some cases, extract the contents of files in a shared drive or quarantined file. Once the contents are base64 encoded, it’s possible to upload them using any API with a file upload capability.
The templates below show how to upload a file to three popular online sandboxes – Cuckoo, App.Any.Run and Hybrid Analysis. In the examples, we replace the base64 encoded contents with the contents from a previous Action, and you can upload to any sandbox. Below you’ll see examples of how to upload to any.run, hybrid analysis, and cuckoo sandbox. There are also templates available for uploading to VirusTotal and several other sandboxes in your Tines tenant.
{
"url": "https://cuckoo.tines.dev:4443/tasks/create/file"
"content_type": "data"
"method": "post"
"payload": {
"file": {
"filename":
"{{.filename}]",
"contents": "{{.base64 encoded _contents | base64 decode}]"
}
},
"headers": {
"Authorization": "Bearer {{CREDENTIAL.cuckoo}}”
}.
"expected_update period_in days": "1"
}{
"url": "https://www.hybrid-analysis.com/api/v2/submit/file"
"content_type": "data"
"method": "post"
"payload": {
"user-agent": "Falcon Sandbox",
"environment id": "110"
"file": {
"contents": "{{.base64 encoded _contents | base64 decode}}"
"filename": "({.filename]]"
}
},
"headers": {
"api-key": "{{CREDENTIAL.hybrid}}"
},
"expected_ update period_in_days": "1"
}{
"url": "https://api.any.run/v1/analysis"
"content_type": "data"
"method": "post",
"payload": {
"file": {
"filename": "{{. filename}}",
"contents":
"{{.base64 _encoded_contents | base64_ decode}}"
}
}.
"headers": {
"Authorization": "API-Key {{CREDENTIAL.ANY_RUN}}"
}.
"expected update period in days": "1"
}Before uploading to any sandbox, we recommend checking to see if the file has been seen before in tools like VirusTotal or Hybrid Analysis or your threat intel platform. If VirusTotal or your threat intelligence platform has seen the file before, we can avoid duplicating work and take response actions immediately. You can read more about VirusTotal automation here.
We can quickly check if a file exists in VirusTotal using the below Action template.
{
"ur": "https://www.virustotal.com/vtapi/v2/file/report",
"method": "get"
"expected_ update_period_in_days": "1",
"payload": {
"apikey": "{{CREDENTIAL.virustotal}}”
"resource": "{{file hash}}"
}
}This template requires the MD5 of the file to check in VirusTotal. If you do not have the MD5 of the file, you can use the Action template below to extract the md5 of a file in Tines.

Note you can also upload files programmatically from a desktop using curl and a command.
Analysis of Manually Uploaded Files
At Tines, we recognize that many processes involve analyzing files found manually – for example, suspicious files found during a breach investigation. This does not mean that the results of the analysis can not be extracted and automated, however. Using Tines, we can extract indicators from every file analyzed in your private sandbox, regardless of how it is submitted.
Analyzing the results of all files uploaded to a Malware Sandbox
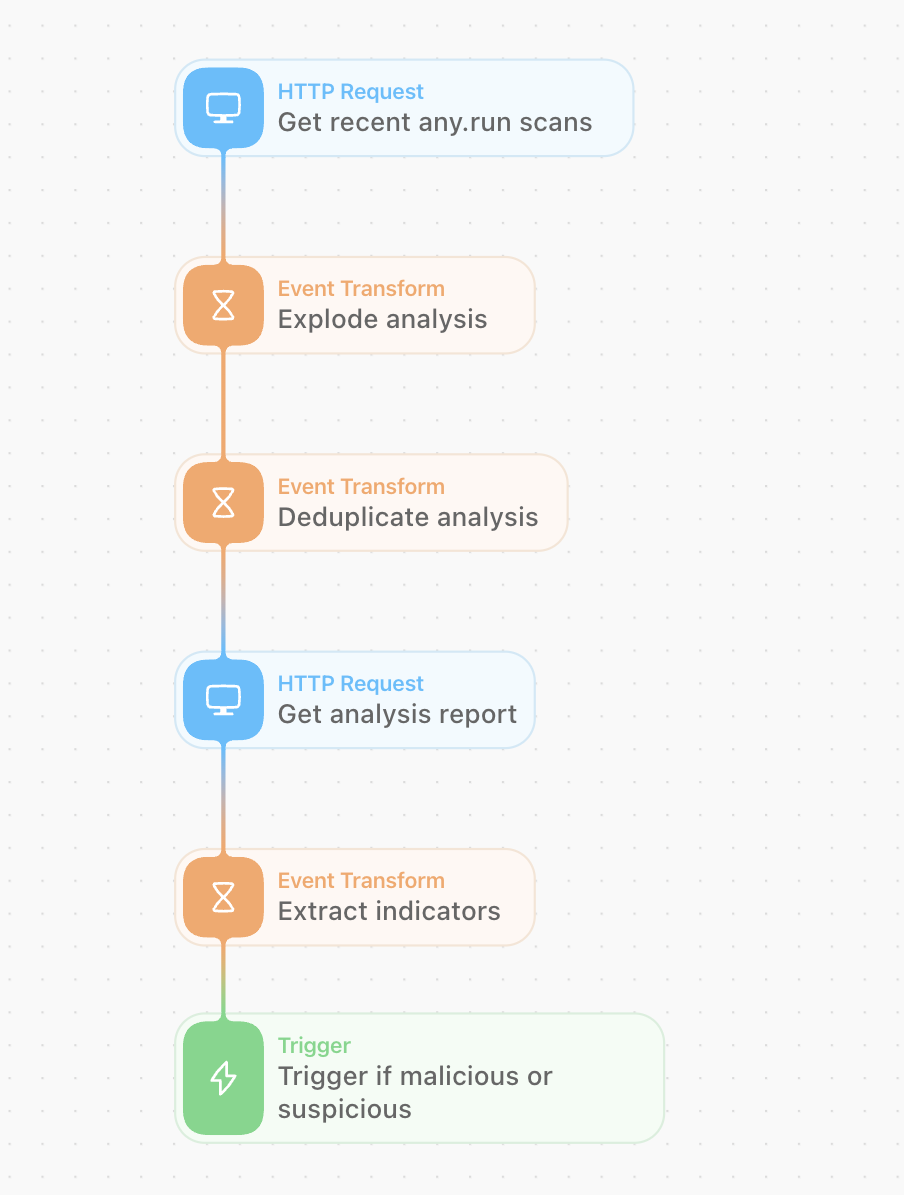
In this Story, we’ve used several liquid filters to extract the relevant elements of the malware analysis report. The best way to automate this in Tines is to create an HTTP Request Action. The HTTP Request Action periodically polls your Sandbox for any new files that have been uploaded. Tines can then extract all the relevant indicators for those reports. The most obvious aim in analyzing malware using a sandbox is to determine its maliciousness. A secondary aim is to extract potential indicators which can be searched for across our environment.
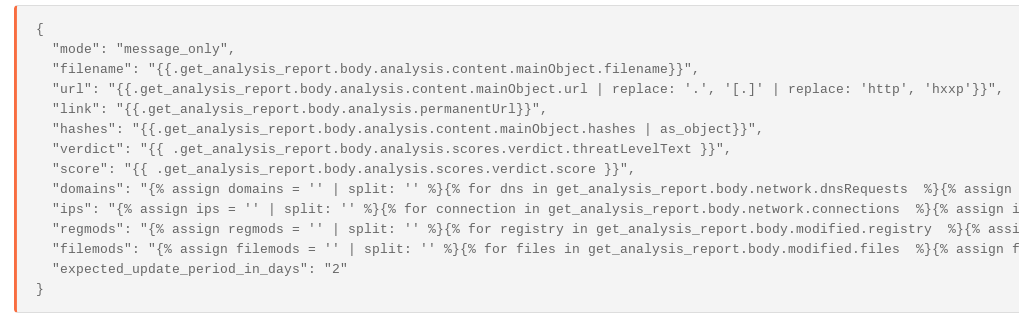
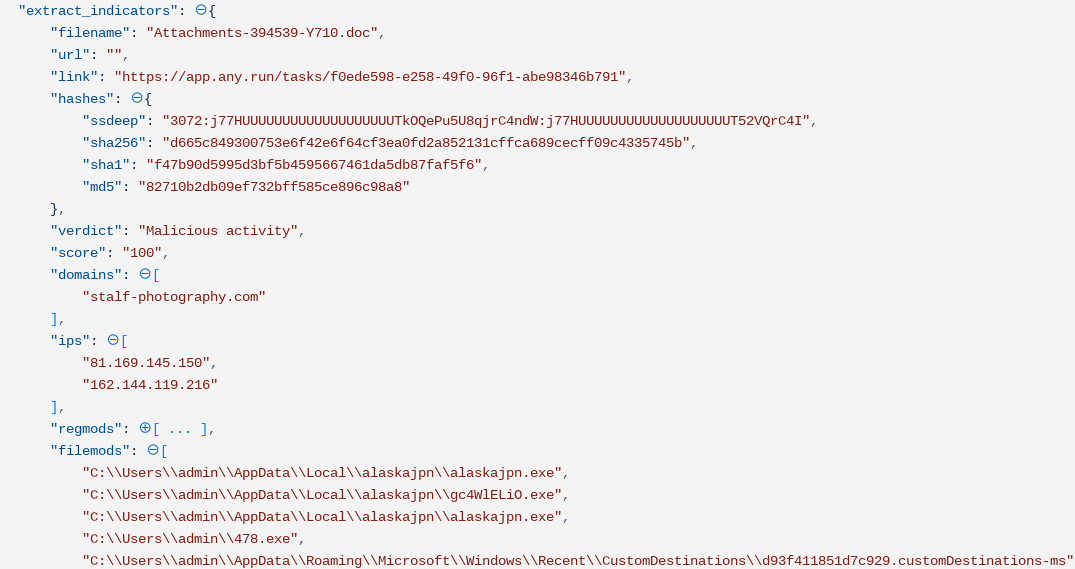
The result is an event that looks like the below – replete with registry modifications, file modifications, network connections, etc. The extracted data is in a format that can then be easily used by other Actions.
Post analysis automation
You can use the results of this file analysis to take other automated Actions in your environment; for example, for every domain, the malware is connected to, you can search for associated traffic to the network indicators. If the file is found to be malicious, you can ban malicious hash from endpoints in your enterprise. You can also search for unique file or registry modifications in an EDR tool, for example. In addition, the Tines Security Automation, Orchestration, and Response platform can use these results to
Isolate or quarantine infected endpoints
Block domains or IP addresses in Firewalls or in DNS tools
Document details about the file to ticketing systems like JIRA, including PCAPs for analysis etc.
Collate all the analyses of multiple to help build better detections of known threats to your environment
Use the detailed results to help prioritize detections using the Mitre Attack Framework
Upload artifacts like malware PCAPs into ServiceNow or Jira, or The Hive
Perform memory dumps on infected endpoints
Block email addresses or domains on your email gateway
In short, automating the malware analysis process can help security operations teams react more quickly to potential threats. This allows them to focus on more impactful, risk-reduction efforts
Note – this should not be taken as a complete method for analyzing malware. The correct approach will depend on your environment and risk tolerance. However, this is illustrative of some of the analyses you can automate using Tines and malware sandboxes.
Conclusion
Malware analysis automation can have several benefits in allowing teams to move quickly and automatically extract the most relevant data from malware reports. Discover ready-to-use automation Stories for malware workflows, VirusTotal, and many more tools in our Story Library.